The massive growth of remote staff in the midst of the COVID-19 has promoted and stimulated the simultaneous growth of cloud services.
Employees that have access to cloud-based networking platforms and software have extended organizational network boundaries to the individual’s residence – a one-man branch office. In light of this, consumers and service providers must refocus their cybersecurity activities in 2021, if they haven’t already.
The key trends to watch for in 2021 in the cyber security landscape are
1) Threats to Cloud
As the coronavirus pandemic accelerated remote work and online teamwork, cloud adoption emerged as an ally for companies seeking to maintain business continuity. Though global companies were transitioning to the cloud prior to the outbreak, the pandemic accelerated the process.
Rapid cloud migration, on the other hand, is expected to bring a slew of new security risks and problems.
As per IDC, in 2021 $1 trillion would be spent in the global cloud services space at a CAGR of 15.7% from 2020-2024.
Web-based security threats such as misconfigured cloud storage, limited access and power, insufficient data deletion, and vulnerable cloud-apps will continue to disrupt companies in the future.
2) Threats from Inside
Staffing demands will be disrupted, and the continuing reliance on a distributed workforce will provide a ripe attack vector for hackers trying to leverage insider attacks. According to Forrester, the remote-workforce movement would lead to an increase in insider attacks. According to them, 25 percent of data breaches are now linked to insider attacks, and that figure is projected to rise to 33 percent by 2021.
Forcepoint predicts the rise of a “insider-as-a-service” model in 2021. This is referred to as orchestrated recruiting infiltrators, which have extremely selective ways for bad actors to become trustworthy employers in order to collect confidential IP.
3)The Advancement In Artificial Intelligence And Machine Learning
Artificial Intelligence (AI) and Machine Learning (ML) have long been recognised as effective methods for detecting and mitigating malicious programs. Machines are being trained to detect threats using both human guidance and trial and error. However, not all applications of AI and ML have been beneficial to mankind. They have not gone unnoticed by cybercriminals, and the application of AI and machine learning has started to pose significant challenges to cybersecurity. To avoid these emerging developments, cybercriminals are using model theft, adversarial inputs, and data poisoning as countermeasures.
4) Cloud Security Posture Management
When the usage of cloud platform technology grows, so does the amount of unmanaged threats in the mission-critical digital sector. Cloud Protection Posture Management (CSPM) automates cloud protection management across a variety of cloud infrastructures.
Via security assessments and automatic compliance reporting, CSPM software enable businesses to detect and remediate threats. Since the cloud ecosystem has grown in scope, organisations should use CSPM to consolidate any potential misconfigurations and ensure compliance with regulations such as GDPR, HIPAA, and CCPA.
The use of CSPM software has several benefits, including:
- Detecting incorrectly configured network connectivity
- Identifying too broad user permissions and assessing data vulnerability
- Constant monitoring of the cloud system for compliance breaches
- In certain instances, the ability to remotely correct misconfigurations
- Observance of common best practices principles
5) Endpoint Management
What is more concerning for businesses is that, in addition to the established bugs and attack vectors, cyber-criminals are discovering new ways to target security gaps caused by the adoption of new technology and work environments. “How do you encrypt the data at the specific edge of your network versus a single large firewall in your data center?” is the big issue for consumers who need to protect remote jobs.
Endpoint management solutions have many advantages to organisations, including the protection of remote workers, management of endpoint settings, automation of provisioning and enforcement, and support for streamlined endpoint troubleshooting.
Remote employees and dispersed applications requiring access to organizational infrastructure necessitate locating, provisioning, distributing, repairing, and troubleshooting endpoint devices within the enterprise from a central location. Endpoint management is critical because cyber attackers will use these endpoints to gain access to business networks.
6) Cloud PKI
Most organizations currently use public key infrastructure (PKI) as a basic security mechanism. However, as IoT, cloud, and DevOps become more prevalent, the function of PKI is shifting.
PKI is a complex system that necessitates safe infrastructure, qualified staff, and the appropriate hardware and software to operate efficiently and effectively. To accomplish this aim with minimal IT and security tools, an increasing number of organisations are migrating their PKI to the cloud.
Cloud infrastructure agility and protection have facilitated highly stable cloud-based PKI deployments hosted and maintained by a trusted partner. Cloud PKI supports companies in a variety of areas, including ensuring smooth and safe processes, lowering costs and accelerating time to value, and saving considerable time and money by offloading labor-intensive PKI administration tasks to the cloud.
Conclusion
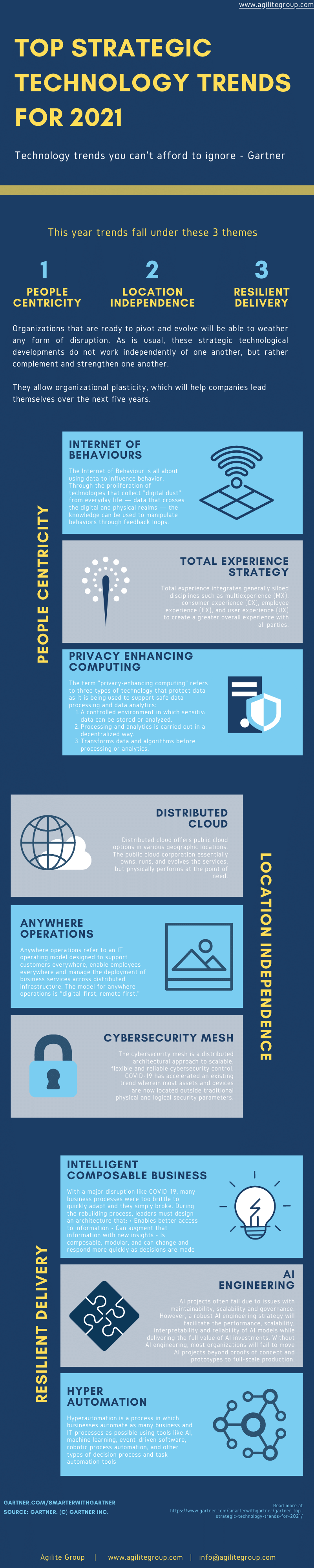
According to Gartner, the cybersecurity developments for 2021 would focus on three concepts.
- People-centeredness. People are at the heart of company activities. To communicate and work in today’s changing world, they must be equipped with digital technologies.
- Freedom from location. A technological change to allow remote business operations.
- Resilience. In an environment that is rapidly changing and unpredictable, you must be able to withstand global threats and uncertainties.
In an environment that is rapidly changing and unpredictable, you must be able to withstand global threats and uncertainties. The main thread running through all of the trends discussed in this article is IDENTITY. You cannot protect the company’s money, value, and image unless you enforce identity security.
It is crucial for a robust corporate cyber security position to secure the digital identity of people and devices/services.